Revealing Program Compatibility Assistant HKCU AppCompatFlags Registry Keys
Tuesday, December 17, 2013
0
comments
The Application Experience and Compatibility feature ensures compatibility of existing software between different versions of the Windows operating system. The implementation of this feature results in some interesting program execution artifacts that are relevant to Digital Forensic and Incident Response (DFIR). I highlighted a Windows 7 artifact in the post Revealing the RecentFileCache.bcf File and Yogesh Khatri highlighted a Windows 8 artifact in his post Amcache.hve in Windows 8 - Goldmine for malware hunters. However, there are still even more artifacts associated with this feature and the AppCompatFlags registry keys are one of them. This post provides some additional information about these registry keys in the Windows 7 and 8 operating systems and the relevance of the data stored within them.
The Program Compatibility Assistant (PCA) is another technology the Windows operating system uses to ensure software compatibility between different Windows versions. The Windows Internals, Part 1: Covering Windows Server 2008 R2 and Windows 7 in the built-in diagnostic utilities section states the following about PCA:
Program Compatibility Assistant (PCA), which enables legacy applications to execute on newer Windows versions despite compatibility problems. PCA detects application installation failures caused by a mismatch during version checks and run-time failures caused by deprecated binaries and User Account Control (UAC) settings. PCA attempts to recover from these failures by applying the appropriate compatibility setting for the application, which takes effect during the next run. In addition, PCA maintains a database of programs with known compatibility issues and informs the users about potential problems at program startup.
The Program Compatibility Assistant is a Windows service. It's service display name is Program Compatibility Assistant Service, service name is PcaSvc and its default description states "this service provides support for the Program Compatibility Assistant (PCA). PCA monitors programs installed and run by the user and detects known compatibility problems. If this service is stopped, PCA will not function properly." The screenshot below shows the Windows 7 PCA service's properties including the path to the executable which is "svchost.exe -k LocalSystemNetworkRestricted."
The article The Program Compatibility Assistant - Part Two goes into a little more detail about how PCA works. It mentions the following:
"When a user launches a program, if that program is on a list of programs that are known to have compatibility issues, then PCA informs the user of this. This list is maintained in the System Application Compatibility Database. Depending on the nature of the issue, the application may be Hard Blocked or Soft Blocked."
A hard block prevents the application from running or installing while a soft block indicates the program has known compatibility issues. The process creation stages were detailed in the post Revealing the RecentFileCache.bcf File; if you are not familiar with the process it's recommend to read the article.
The Program Compatibility Assistant uses compatibility modes to help programs run on Windows. These compatibility modes are set in the following registry keys (which one is used depends on if the setting is for all users or the current user):
HKLM\ Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers
HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers
For each compatibility setting there is a registry value listed beneath the Layers registry key. The value contains: the path to the executable and the compatibility mode being applied. To illustrate how this works I'll walk through the FTK imager installation process on a Windows 7 system. The picture below shows FTK imager's file properties with the Windows XP (Service Pack 3) compatibility mode selected. This setting only applies to the current user; for it to apply to all users the "Change settings for all users" must be used.
After applying the compatibility setting the registry value is updated beneath the Layers key as shown below.
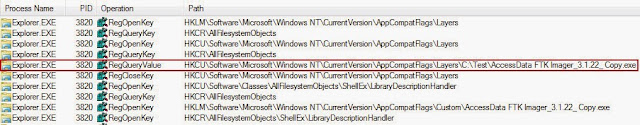
This compatibility setting is queried during the process creation stages. The image below shows Explorer.exe starting the AccessData FTK Imager_3.1.22_Copy.exe process.
The image below shows the compatibility setting being queried during the process creation.
The article The Program Compatibility Assistant - Part Two goes into further detail about how PCA works. Besides the Layers registry key, " PCA stores the list of all programs for which it came up under the following key for each user, even if no compatibility modes were applied (in other words, the user indicated that the program worked correctly)." In Windows 7, it appears that PCA records the programs that have an installation routine inside the user account registry hive it executed under. The registry location is:
HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Persisted
To illustrate how this works I'll again walk through the FTK imager installation process on a Windows 7 system. (note: I tested various programs without installation routines but none of them were recorded in the Windows 7 Persisted registry key). The image below shows the FTK imager process starting.
The next image shows the Application Experience service modifying the RecentFileCache.bcf file since the AccessData FTK Imager_3.1.22.exe file was recently created.
Up to this point in the process creation it is very similar to what I described in the post about the RecentFilecache.bcf file. However, the next image shows the PCA process becoming more active.
The properties of the svchost.exe process confirms it is in fact the Program Compatibility Assistant service as shown below:
The PCA service performs various activities as the FTK Imager application starts to load. One of those activities is querying the registry key HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Persisted as shown below:
Shortly thereafter the PCA service modifies the Persisted registry key as shown below.
This modification is to record the AccessData FTK Imager_3.1.22.exe file that executed on the system. The other programs listed in the Persisted registry key all had installation routines when they executed.
In Windows 8, the Program Compatibility Assistant appears to function similar to the process I described previously. However, there is one key difference in Windows 8. It appears that PCA records all third party programs inside the user account registry hive it executed under regardless if it has an installation routine or not. The Persisted registry key is no longer present and the data is stored in the location below:
HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store
To illustrate how this works I'll through the Process Explorer program executing on a Windows 8 system. Process Explorer is a standalone program so it doesn't have an installation routine. The walkthrough I'm doing is very similar to programs with installation routines running on Windows 8. The image below shows the Process Explorer starting.
For brevity I'm excluding other images in the process creation and only showing the activity related to PCA. The image below shows PCA accessing the application compatibility database.
PCA continues by querying the File registry key inside the Amcache.hve registry hive. In Windows 8, this registry hive replaces the RecentFilecache.bcf file. For more information about this new artifact refer to the posts: Yogesh Khatri's Amcache.hve in Windows 8 - Goldmine for malware hunters and Amcache.hve - Part 2.
PCA queries various locations as Process Explorer starts to load; one of them is the registry key HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store as shown below.
The other activity PCA does with the store registry key is to record information about Process Explorer as shown below.
Looking at the registry values in the Store registry key shows it contains references to various third party applications. The applications are ones without installation routines (procmon.exe, Tweb.exe, and procexp.exe) as well as ones with installation routines (FTK imager and FoxIt). The Store registry key even ties applications to Internet Explorer (Tweb.exe).
The AppCompatFlags registry keys' are another artifact that shows program execution. The following are some of the relevant registry keys:
HKLM\ Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers
HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers
HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Persisted
HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store
The relevance of the executables listed in these keys mean the following:
1. The program executed on the system.
2. The program executed on the system under the user account where the keys are located
Exploring the Program Compatibility Assistant
The Program Compatibility Assistant (PCA) is another technology the Windows operating system uses to ensure software compatibility between different Windows versions. The Windows Internals, Part 1: Covering Windows Server 2008 R2 and Windows 7 in the built-in diagnostic utilities section states the following about PCA:
Program Compatibility Assistant (PCA), which enables legacy applications to execute on newer Windows versions despite compatibility problems. PCA detects application installation failures caused by a mismatch during version checks and run-time failures caused by deprecated binaries and User Account Control (UAC) settings. PCA attempts to recover from these failures by applying the appropriate compatibility setting for the application, which takes effect during the next run. In addition, PCA maintains a database of programs with known compatibility issues and informs the users about potential problems at program startup.
The Program Compatibility Assistant is a Windows service. It's service display name is Program Compatibility Assistant Service, service name is PcaSvc and its default description states "this service provides support for the Program Compatibility Assistant (PCA). PCA monitors programs installed and run by the user and detects known compatibility problems. If this service is stopped, PCA will not function properly." The screenshot below shows the Windows 7 PCA service's properties including the path to the executable which is "svchost.exe -k LocalSystemNetworkRestricted."
The article The Program Compatibility Assistant - Part Two goes into a little more detail about how PCA works. It mentions the following:
"When a user launches a program, if that program is on a list of programs that are known to have compatibility issues, then PCA informs the user of this. This list is maintained in the System Application Compatibility Database. Depending on the nature of the issue, the application may be Hard Blocked or Soft Blocked."
A hard block prevents the application from running or installing while a soft block indicates the program has known compatibility issues. The process creation stages were detailed in the post Revealing the RecentFileCache.bcf File; if you are not familiar with the process it's recommend to read the article.
Exploring the HKU AppCompatFlags Layers Registry Keys
The Program Compatibility Assistant uses compatibility modes to help programs run on Windows. These compatibility modes are set in the following registry keys (which one is used depends on if the setting is for all users or the current user):
HKLM\ Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers
HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers
For each compatibility setting there is a registry value listed beneath the Layers registry key. The value contains: the path to the executable and the compatibility mode being applied. To illustrate how this works I'll walk through the FTK imager installation process on a Windows 7 system. The picture below shows FTK imager's file properties with the Windows XP (Service Pack 3) compatibility mode selected. This setting only applies to the current user; for it to apply to all users the "Change settings for all users" must be used.
After applying the compatibility setting the registry value is updated beneath the Layers key as shown below.
This compatibility setting is queried during the process creation stages. The image below shows Explorer.exe starting the AccessData FTK Imager_3.1.22_Copy.exe process.
The image below shows the compatibility setting being queried during the process creation.
Exploring the Windows 7 AppCompatFlags Persisted Registry Key
The article The Program Compatibility Assistant - Part Two goes into further detail about how PCA works. Besides the Layers registry key, " PCA stores the list of all programs for which it came up under the following key for each user, even if no compatibility modes were applied (in other words, the user indicated that the program worked correctly)." In Windows 7, it appears that PCA records the programs that have an installation routine inside the user account registry hive it executed under. The registry location is:
HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Persisted
To illustrate how this works I'll again walk through the FTK imager installation process on a Windows 7 system. (note: I tested various programs without installation routines but none of them were recorded in the Windows 7 Persisted registry key). The image below shows the FTK imager process starting.
The next image shows the Application Experience service modifying the RecentFileCache.bcf file since the AccessData FTK Imager_3.1.22.exe file was recently created.
Up to this point in the process creation it is very similar to what I described in the post about the RecentFilecache.bcf file. However, the next image shows the PCA process becoming more active.
The properties of the svchost.exe process confirms it is in fact the Program Compatibility Assistant service as shown below:
The PCA service performs various activities as the FTK Imager application starts to load. One of those activities is querying the registry key HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Persisted as shown below:
Shortly thereafter the PCA service modifies the Persisted registry key as shown below.
This modification is to record the AccessData FTK Imager_3.1.22.exe file that executed on the system. The other programs listed in the Persisted registry key all had installation routines when they executed.
Exploring the Windows 8 AppCompatFlags Store Registry Key
In Windows 8, the Program Compatibility Assistant appears to function similar to the process I described previously. However, there is one key difference in Windows 8. It appears that PCA records all third party programs inside the user account registry hive it executed under regardless if it has an installation routine or not. The Persisted registry key is no longer present and the data is stored in the location below:
HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store
To illustrate how this works I'll through the Process Explorer program executing on a Windows 8 system. Process Explorer is a standalone program so it doesn't have an installation routine. The walkthrough I'm doing is very similar to programs with installation routines running on Windows 8. The image below shows the Process Explorer starting.
For brevity I'm excluding other images in the process creation and only showing the activity related to PCA. The image below shows PCA accessing the application compatibility database.
PCA continues by querying the File registry key inside the Amcache.hve registry hive. In Windows 8, this registry hive replaces the RecentFilecache.bcf file. For more information about this new artifact refer to the posts: Yogesh Khatri's Amcache.hve in Windows 8 - Goldmine for malware hunters and Amcache.hve - Part 2.
PCA queries various locations as Process Explorer starts to load; one of them is the registry key HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store as shown below.
The other activity PCA does with the store registry key is to record information about Process Explorer as shown below.
Looking at the registry values in the Store registry key shows it contains references to various third party applications. The applications are ones without installation routines (procmon.exe, Tweb.exe, and procexp.exe) as well as ones with installation routines (FTK imager and FoxIt). The Store registry key even ties applications to Internet Explorer (Tweb.exe).
AppCompatFlags Registry Keys' Relevance
The AppCompatFlags registry keys' are another artifact that shows program execution. The following are some of the relevant registry keys:
HKLM\ Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers
HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Layers
HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Persisted
HKCU\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store
The relevance of the executables listed in these keys mean the following:
1. The program executed on the system.
2. The program executed on the system under the user account where the keys are located
Labels:
program execution